USB attacks explained (Krzysztof Opasiak, LVEE-2017)
Материал из 0x1.tv
Короткая ссылка: 20170424F
- Speaker
- Krzysztof Opasiak
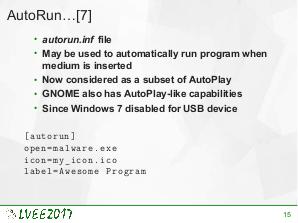
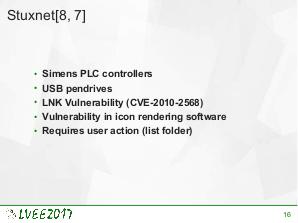
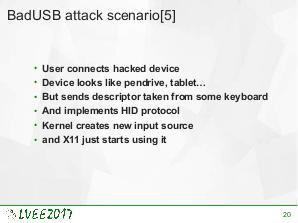
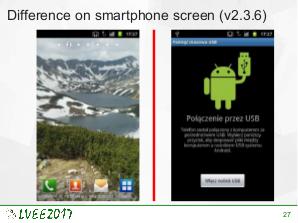
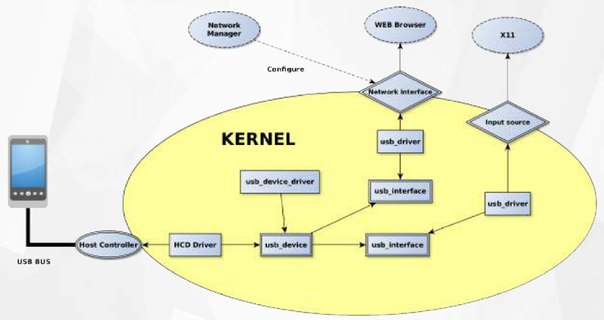
USB is the most common external interface in the world. Even machines which, for security reasons, are disconnected from the Internet often offer USB connectivity. This creates a new attacks surface for skilled hackers. USB implementation may be exploited on various levels. To effectively protect against such attack, knowledge about already exploited vulnerabilities is required. This paper is a survey of state-of-the-art USB-related attacks.
Video[править вики-текст]
Slides[править вики-текст]
Thesis[править | править вики-текст]
Links[править вики-текст]
Plays:116 Comments:0