USB attacks explained (Krzysztof Opasiak, LVEE-2017) — различия между версиями
Материал из 0x1.tv
StasFomin (обсуждение | вклад) |
StasFomin (обсуждение | вклад) (Batch edit: replace PCRE \{\{youtubelink\|([^\}]*)\}\} with {{youtubelink|\1}}{{letscomment}}) |
||
;{{SpeakerInfo}}: {{Speaker|Krzysztof Opasiak}}
<blockquote>
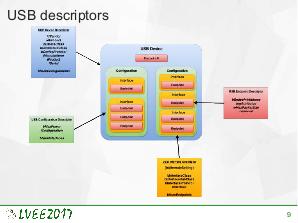
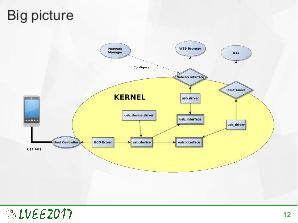
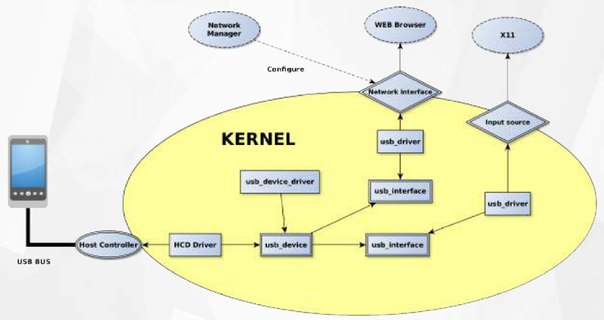
USB is the most common external interface in the world. Even machines which, for security reasons, are disconnected from the Internet often offer USB connectivity. This creates a new attacks surface for skilled hackers. USB implementation may be exploited on various levels. To effectively protect against such attack, knowledge about already exploited vulnerabilities is required. This paper is a survey of state-of-the-art USB-related attacks.
</blockquote>
{{VideoSection}}
{{vimeoembed|223913380|800|450}}
{{youtubelink|hjaVq3w_Tus}}{{letscomment}}
{{SlidesSection}}
[[File:USB attacks explained (Krzysztof Opasiak, LVEE-2017).pdf|left|page=-|300px]]
{{----}}
== Thesis == | |||
Версия 16:59, 19 октября 2018
- Speaker
- Krzysztof Opasiak
USB is the most common external interface in the world. Even machines which, for security reasons, are disconnected from the Internet often offer USB connectivity. This creates a new attacks surface for skilled hackers. USB implementation may be exploited on various levels. To effectively protect against such attack, knowledge about already exploited vulnerabilities is required. This paper is a survey of state-of-the-art USB-related attacks.
Video
Посмотрели доклад? Понравился? Напишите комментарий! Не согласны? Тем более напишите.
Slides
Thesis
Links
Plays:58
Comments:0