USB attacks explained (Krzysztof Opasiak, LVEE-2017) — различия между версиями
Материал из 0x1.tv
StasFomin (обсуждение | вклад) |
StasFomin (обсуждение | вклад) |
||
{{eng}} ;{{SpeakerInfo}}: {{Speaker|Krzysztof Opasiak}} <blockquote> USB is the most common external interface in the world. Even machines which, for security reasons, are disconnected from the Internet often offer USB connectivity. This creates a new attacks surface for skilled hackers. USB implementation may be exploited on various levels. To effectively protect against such attack, knowledge about already exploited vulnerabilities is required. This paper is a survey of state-of-the-art USB-related attacks. </blockquote> {{VideoSection}} {{vimeoembed|223913380|800|450}} <!-- {{youtubelink|}} --> {{SlidesSection}} [[File:USB attacks explained (Krzysztof Opasiak, LVEE-2017).pdf|left|page=-|300px]] {{----}} == Thesis == {{LinksSection}} * [https://lvee.org/ru/abstracts/243 Talks page] <!-- <blockquote>[©]</blockquote> --> <references/> {{stats|youtube_plays=0|refresh_time=2017-07-06T14:16:40.365000|vimeo_plays=0}} [[Категория:Linux]] [[Категория:Open-source]] [[Категория:LVEE-2017]] [[Категория:Draft]] | |||
Версия 16:35, 8 июля 2017
- Speaker
- Krzysztof Opasiak
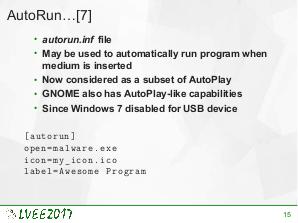
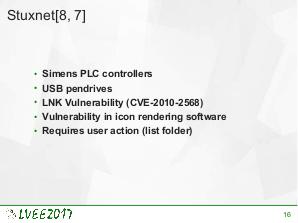
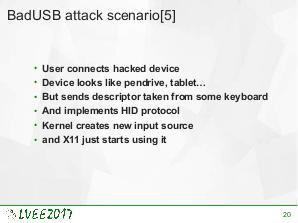
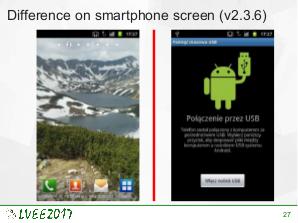
USB is the most common external interface in the world. Even machines which, for security reasons, are disconnected from the Internet often offer USB connectivity. This creates a new attacks surface for skilled hackers. USB implementation may be exploited on various levels. To effectively protect against such attack, knowledge about already exploited vulnerabilities is required. This paper is a survey of state-of-the-art USB-related attacks.
Video
Slides
Thesis
Links
Plays:0
Comments:0